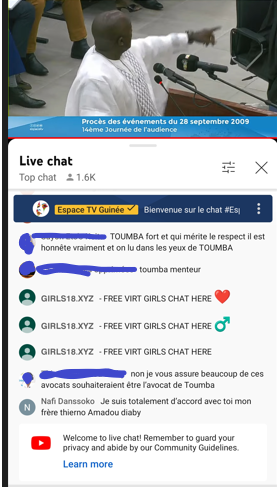
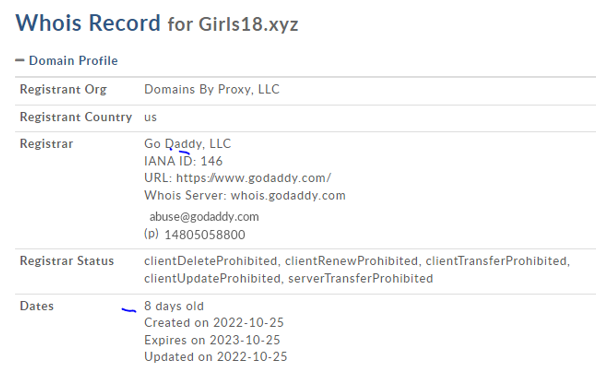
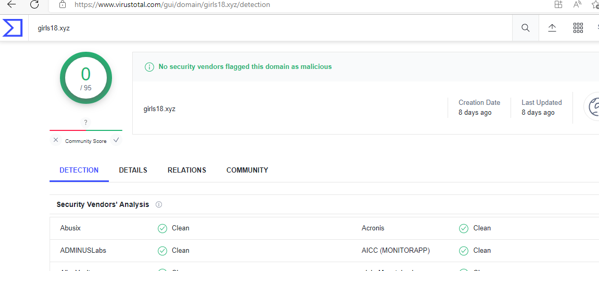
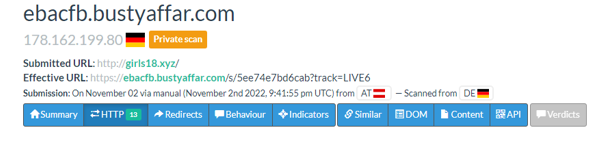
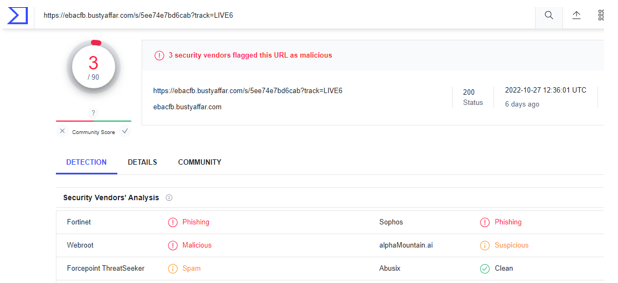
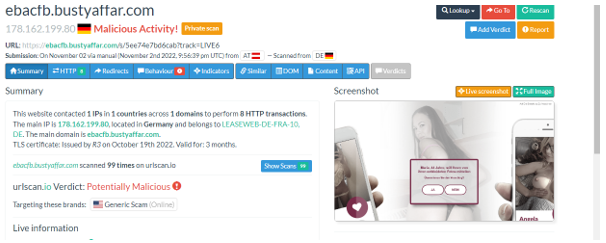
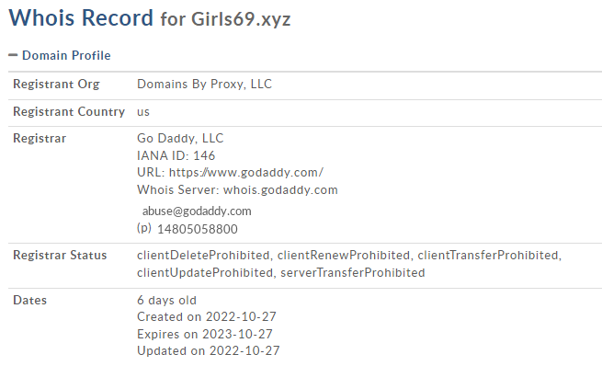
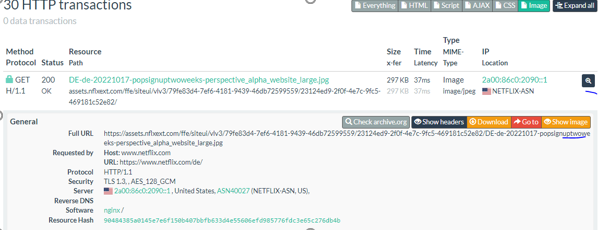
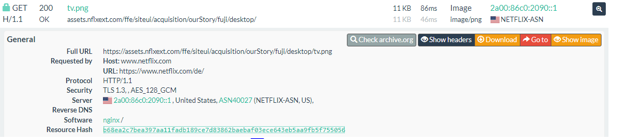
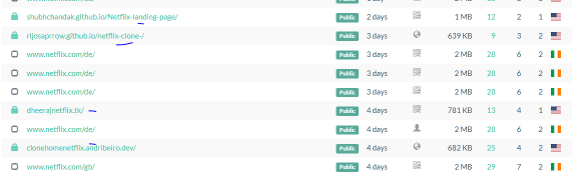
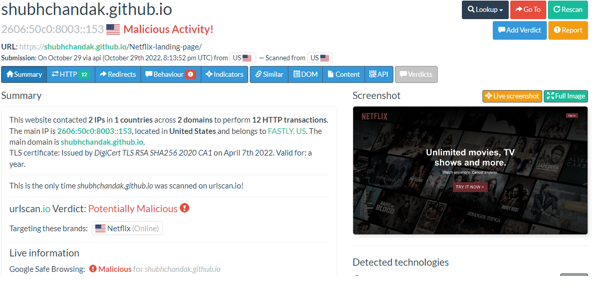
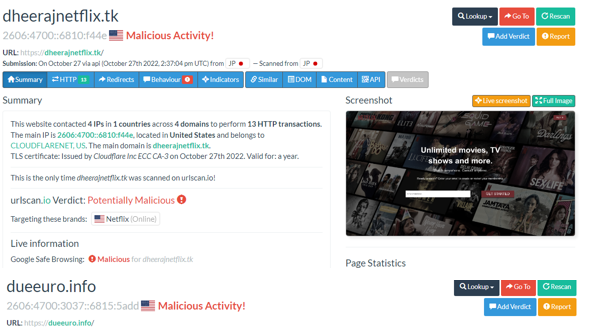
OpenSSL has patched two high severity vulnerabilities

OpenSSL has released two high severity vulnerabilities within the open source OpenSSL library.
The both vulnerabilities CVE-2022-3602 and CVE-2022-3786 require a malicious X.509 certificate that has been signed by a valid certificate authority.
The first vulnerability CVE-2022-3602 - could cause a denial of service by allowing the bytes containing the character “.” (decimal 46) to be entered on the stack.
The second one CVE-2022-3786 - could cause a denial of service by allowing the attacker to craft a malicious email address in a certificate to overflow an arbitrary number of bytes containing the “.” character (decimal 46) on the stack.
Affected version: OpenSSL versions 3.0.0 to 3.0.6.
Mitigation: OpenSSL 3.0 users should upgrade to OpenSSL 3.0.7.
 Best OSINT tools to investigate Typo squatting domains
Best OSINT tools to investigate Typo squatting domains  Top Free Threat Intelligence Feeds for SOC
Top Free Threat Intelligence Feeds for SOC  Best WordPress website scanner for free
Best WordPress website scanner for free  Phishing as a service platforms used by threat actors
Phishing as a service platforms used by threat actors  Fake Microsoft Teams website to deliver malware
Fake Microsoft Teams website to deliver malware